-
Log on to the SAML SSO page of the SkyVault Admin Console with your user
credentials:
http://localhost:8080/alfresco/service/enterprise/admin/admin-saml
where localhost:8080 is your SkyVault host name and port.
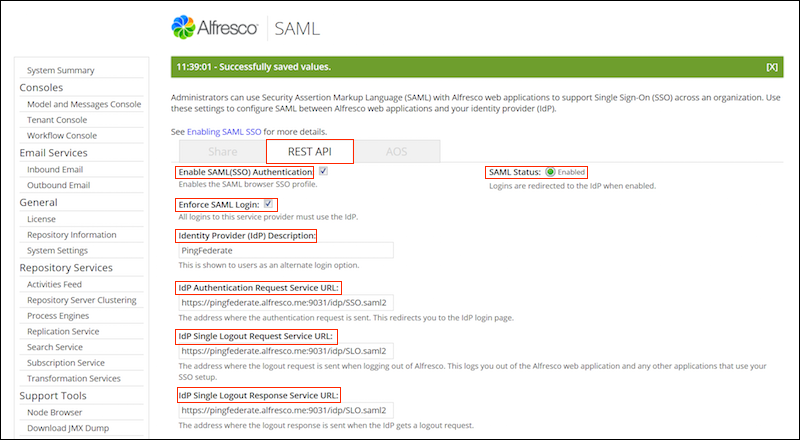
- Select the REST API tab.
-
Select Enable SAML (SSO) Authentication.
SAML Status shows whether SAML is currently enabled or disabled.
-
(Optional) Select Enforce SAML Login.
If this option is selected by default then all logins to this service provider must use the Identity Provider (IdP). If you do not enforce the SAML login, the user can decide to use either the SkyVault login or login using the IdP link.
-
Specify the Identity Provider (IdP) Description.
This description is shown to users as an alternate login option when Enforce SAML Login is deactivated. If no description is provided, the text displayed on the SkyVault login screen would read your single sign-on provider. Clicking on this description will redirect you to the IdP.
-
Enter the IdP settings:
- IdP Authentication Request Service URL: The address where the authentication request is sent. This redirects you to the identity provider login page.
- IdP Single Logout Request Service URL: The address where the logout request is sent when logging out of SkyVault. This logs you out of SkyVault and any other applications that use your SSO setup.
- IdP Single Logout Response Service URL: The address where the logout response is sent when the identity provider gets a logout request.
- Entity Identification (Issuer): Some IdPs use the issuer to determine which service provider connection to use. If you are using AD FS, this is the Base URL (http://localhost:8080/SkyVault where localhost:8080 is your SkyVault host name and port).
- User ID Mapping: The SAML attribute that maps to a SkyVault User ID. For PingFederate, this maps to PersonImmutableID. For AD FS, the SAML attribute is the Subject/NameID specified for the SAML subject NameID.
-
Click Upload IdP Certificate to browse to and upload the IdP
certificate that you downloaded from your IdP in Exporting your IdP certificate.
IdP Certificate Status shows whether the certificate is valid, and IdP Certificate Status shows the expiry date of the current certificate.
SkyVault does not allow you to upload an expired certificate. If you attempt to do this, you will see an error message.
Note: If SAML is enabled, SkyVault always checks for a existing certificate. -
Click Download SP Certificate to download the certificate
required by your IdP.
This is a copy of your self-signed certificate. You already downloaded this information when setting up your connections in the IdP here: Configuring PingFederate manually.
-
Click Download SP Metadata if you need to download the
service provider signature verification certificate.
This is required for AD FS configuration, if you are using AD FS as your IdP.
- Click Save.
You have configured the SAML SSO settings. You can disable these settings by deselecting Enable SAML (SSO) Authentication.
http://localhost:8080/alfresco/service/saml/-default-/rest-api/enabledwhere:
- -default- is the tenant name
- rest-api is the id of our SAML REST API SP
{
"entry":
{
"isSamlEnabled": true,
"isSamlEnforced": true,
"idpDescription": ".....",
"tenantDomain": "...."
}
}
